A brute force attack is a common way of cracking or guessing usernames and passwords to acquire illegal access to a system. According to some estimates, brute force attacks accounted for 5% of verified security breaches.
These are “brute force” cyberattacks, which involve very aggressive attempts to “force” their way into your private account (s). Attacks that use brute force to guess a password are as old as the concept of a password itself. As the trend toward remote work grows, so does their popularity.

What do hackers achieve by using brute force?
These techniques need some effort from brute-force attackers in order to be successful. Despite the fact that technology makes it simpler, you may still wonder: why would someone do this?
Here’s how brute force tactics help hackers:
Ads or data collection Hackers can exploit websites for advertising commissions. Popular methods include spamming adverts on popular websites to gain money when clicked or watched. Traffic reroutes to ad sites. Infecting a site or visitors with activity-tracking spyware.
Data and assets stolen. Everything from bank accounts to tax information may be obtained online. Criminals may steal your name, money, or private credentials with the perfect break-in. Corporate-level data breaches can expose sensitive information from whole sectors.
Spreading malware for fun. Hackers reroute website traffic to malicious sites to create trouble or learn. They may also infect a website with malware to install on visitors’ PCs.
Malicious system hijacking. When one computer isn’t enough, hackers use a network to speed up their work. Malware may infect your computer, mobile device, or online accounts with spam, phishing, and more. Without an antivirus, your chance of infection increases.
Reputation-killing a website. A cybercriminal may post indecent material on your website. This includes violent, pornographic, or racially insulting language, pictures, and audio.
List of Possible Brute Force Attacks
Different strategies can be used by different brute force attacks to discover your private information. Some of the most common brute force approaches include:
- Simple Brute Force Attacks
- Hybrid Brute Force Attacks
- Dictionary Attacks
- Credential Stuffing
- Reverse Brute Force Attacks
Simple Brute Force Attacks
Hackers attempt to deduce your credentials logically, without any assistance from software tools or other means.
It works by following an algorithmic process rather than using outside logic to make guesses. These can expose passwords and PINs that are really basic. For instance, a password set as “user12345.”
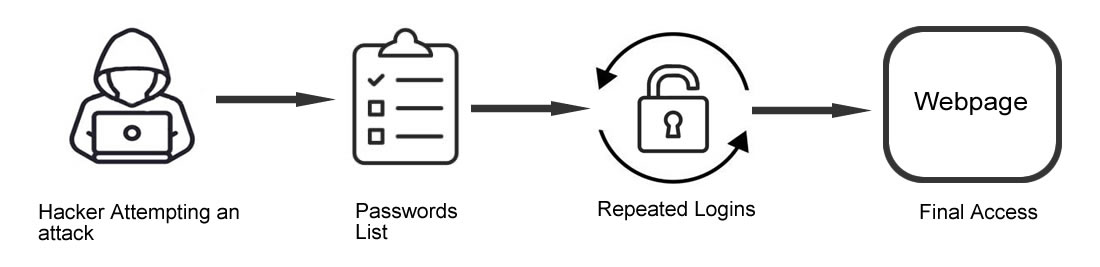
To break passwords, a programme or script (bot) is started which tries every potential combination of numbers, letters, and characters to find the right one. As many passwords are weak and similar, lists of frequently used credentials or passwords that have been stolen can be used to increase the chances of success.
Hybrid Brute Force Attacks
These hackers seek to break into a system by combining their logical assumptions with outside resources. Both hybrid attacks and brute force assaults are commonly used in hybrids.
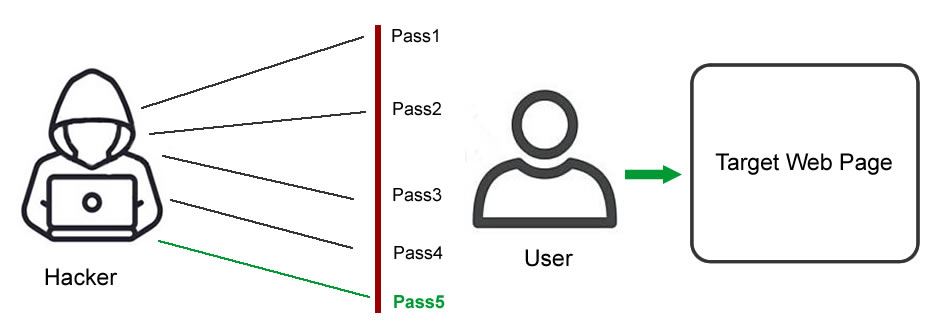
A combination of popular words and random characters can be found using these attacks. It starts with external logic to select the most likely password variant, then tries many.
There are two types of reverse brute force attacks: those that employ dictionaries, and those that use brute force attacks. As opposed to brute force or dictionary attacks, this is a more efficient method.
Dictionary Attacks
It uses a dictionary of relevant strings or phrases to guess usernames or passwords. A hacker runs potential passwords against a username in a conventional attack. Dictionary attacks are simple brute force attacks and are used to break passwords. Some hackers use whole dictionaries and add special characters and numbers to words, which is a hard way to attack in a sequential way.
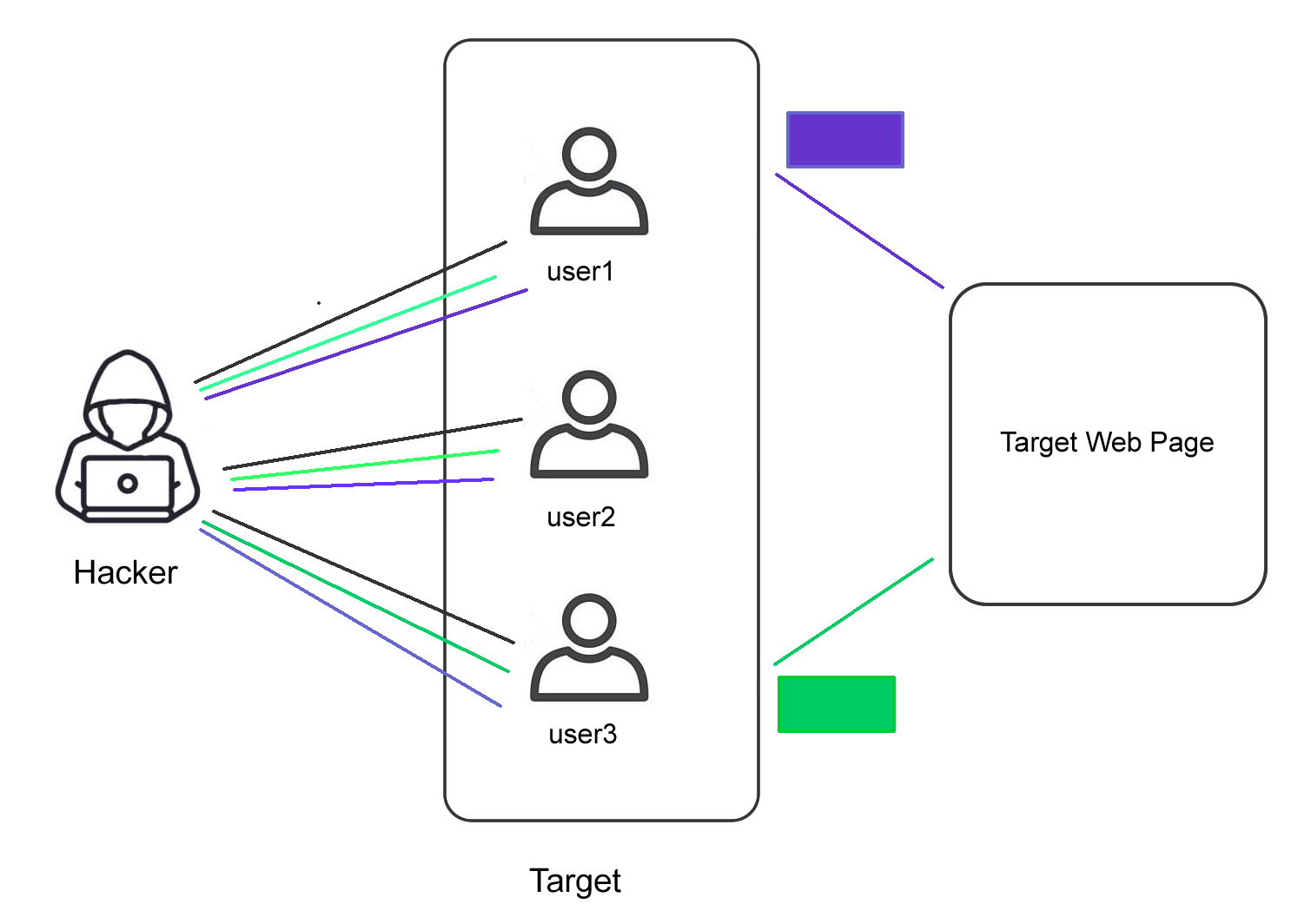
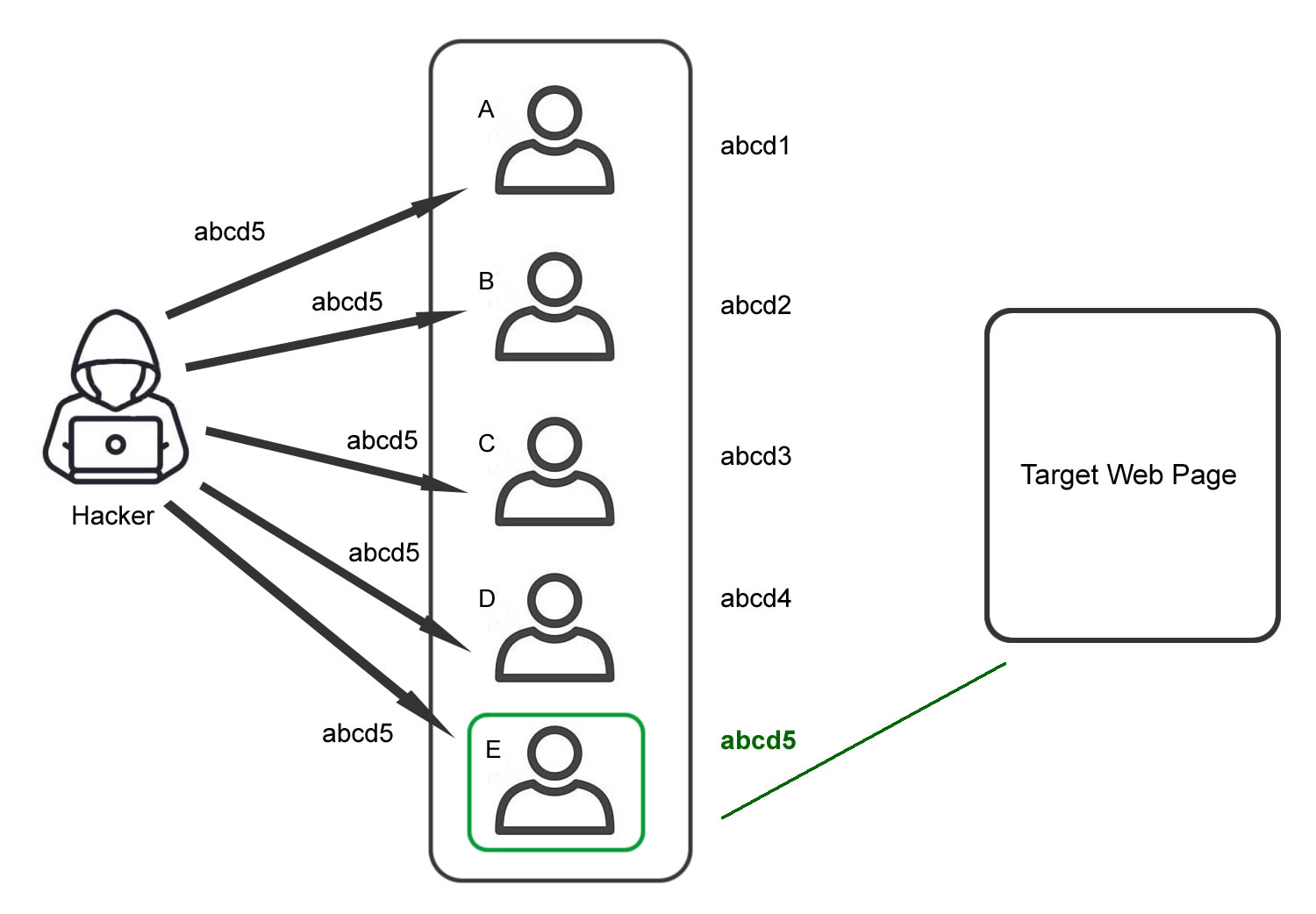
Credential Stuffing
Assumes many people use the same login and password on several systems.
One username-password combination that works on one website is going to be tested across the board by hackers. Because of the prevalence of people reusing their login credentials across several websites, an attack like this is aimed solely at them.
Consumers and businesses alike are at risk because of the long-term consequences of credential stuffing.
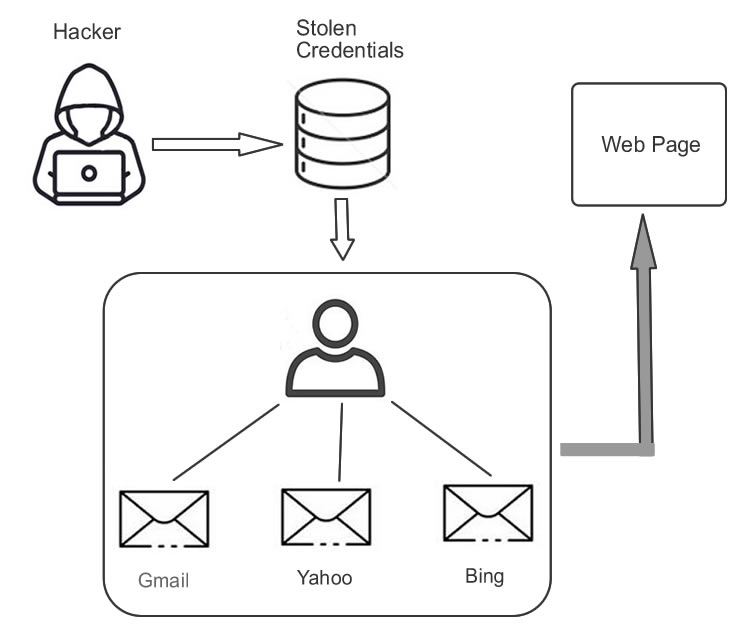
Credential Stuffing Attempts works as follows
Credential stuffing attacks are often carried out in the following manner by an attacker. The armed robber:
- To automate the login of numerous users at the same time using a spoofed IP address, use a bot.
- It checks a large number of websites to see if credentials stolen are valid using an automated procedure. Parallel processing makes it less necessary to keep logging into the same service over and over.
- Personal information, credit cards, or other important data can be retrieved from hacked accounts.
- For example, phishing attempts or other transactions made possible by the hacked service may be able to access your account information in the future.
Reverse Brute Force Attacks
Starting with a known password in a reverse brute force attempt is exactly what the name indicates. In order to locate a match, hackers browse through a million usernames at once. Many of these attackers start with leaked passwords from data breaches that have happened in the past.
To put it another way, a reverse brute-force attack is the exact opposite of a brute-force attack. Brute-force attacks begin with the hacker knowing the username and guessing the password, rather than the other way around. Trial and error is the most common method of guessing a password.
Testing Brute Force Attacks
Various tools are employed by brute-force attackers to achieve their objectives. These brute-force attack tools can be used for penetration. “Pentesting” or “pen testing” is another term for this type of testing.
Fail2ban is a firewall that keeps unauthorized people from getting into a server’s open ports and services that are already running.
By monitoring service logs for suspicious behavior, Fail2ban can assist in preventing brute-force and other automated assaults on your Linux system. Log files are scanned using regular expressions by utilizing this tool. Failing to meet a certain threshold results in the IP address being blocked for a predetermined period of time by Fail2ban’s system firewall.
A user’s IP address gets removed from the list of banned IP addresses when the ban time has expired.
Fail2ban installation
Fail2ban can be installed with the following command:
apt install fail2ban
After installation, it begins shortly. Use the following command to see if the service is running:
systemctl status fail2ban
Fail2ban configuration
Copy the jail.conf file to update the ban settings for all services.
cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
Go to the [DEFAULT] section in the jail.local file. Let’s say the ban period is set at 3600 minutes, for example.
bantime = 3600m
JAILS is where you’ll find a complete list of rules. As an example:
[nginx-http-auth]
Restart the service after making the necessary changes.
systemctl restart fail2ban
Adding and configuring rules
For maintaining active rules, there is a.d/ subdirectory in the /etc/fail2ban/jail directory. Each of them can be saved in an own file. For instance, nginx-http-auth.conf. Another option is to edit the defaults-debian.conf file and add new configuration. Simply insert the following text:
Each rule has its own set of parameters, which you may provide here.
[nginx-http-auth]
enabled = true
There are 10 unsuccessful authorisation attempts, therefore we’ll ban them for 2400 minutes with the ignoreip option set to ignore IP addresses.
ignoreip = 10.10.10.5
bantime = 2400m
maxretry = 10
Save and close the file and restart the service.
systemctl restart fail2ban
Using fail2ban-client
Managing the rules of Fail2ban may be done using a client application. In the event of a system reboot or service restart, any modifications made here will be lost. See what regulations are currently in place by typing:
fail2ban-client status
Use this command instead of sshd to get the stats of your jail:
fail2ban-client status sshd
To make a rule active, enter the command and the rule’s name from the configuration file:
fail2ban-client add nginx-http-auth
Then start it.
fail2ban-client start nginx-http-auth
To view all available commands:
fail2ban-client -h
Top Software for pentesting
BruteX is an open-source, all-in-one brute force shell-based programme that may be used to accomplish any task.
Penetration testers will greatly benefit from using this tool. Nmap, Hydra, and DNSenum are all included in this bundle. Using brutex, you may begin scanning your target using Nmap, and then brutex will force any open services, such as FTP or SSH, on the target.
How To Prevent Brute Force Attacks
For obvious reasons, both enterprises and individuals are concerned about password hacks of this sort. The good news is that brute-force attacks can be stopped in a number of ways, such as:
- Use passwords that are difficult for your users to guess. Use passphrases, which are more secure than typical passwords since they’re longer and simpler to remember.
- Avoid storing user credentials on servers that are visible to the public. Even passwords that are encrypted or hashed and stored online can be broken into with tools like rainbow tables.
- Change the URLs for online applications and services. It’s not a foolproof solution, but it does discourage dumb hackers from hitting your site with automated brute force attacks.
- Tools like reCAPTCHA require users to perform basic tasks before they can log in. These jobs can be completed by humans, but brute force tools are unable to.
- Use account controls and follow best practices for access controls. As a result, you can be certain that only those with the proper credentials have access to the IT systems of your company.
- Limit the number of times a user tries to log in to their account by setting a policy. Set a limit on how many erroneous or unsuccessful login attempts a single user profile may make in a certain time period, whether it’s three or ten.
- Multifactor authentication is a wise practice. A brute force attempt is less likely to succeed when users are forced to provide more than one form of authentication, such as a password plus a fingerprint or a one-time security token.
- When feasible, use user certificates for authentication. Because certificate-based authentication uses a large key, brute-force attacks are practically impossible, and this isn’t prone to phishing or data breaches.
Conclusion:
An attack that employs brute force is a method of guessing data such as login passwords and encryption keys by making a series of failed attempts. The attacker tries a variety of usernames and passwords until they get it right.
Making your passwords as strong as possible will help prevent a brute force attack since it will take longer for hackers to get into your account and make it more likely that they will stop trying.